Forum tip: Always check when replies were posted. Technology evolves quickly, so some answers may not be up-to-date anymore.
-
Newbie Guide to Unattended Remote AccessJust updated to the new 2.2 version and it started working well again - asking for Windows user password.
-
Newbie Guide to Unattended Remote AccessOn the very first screenshot (host computer) you can see an option for "Encryption reguired" is switched On and you can see a part of encryption key actually. The second screenshot (in the middle) is from a computer trying to access the first one. It has also encryption reguired option and the key is the same. And as you can see on the third screenshot, the host computer is still requesting PIN.
-
Newbie Guide to Unattended Remote AccessAs you can see in the screenshots on previous posts I am using encryption key.
-
Newbie Guide to Unattended Remote AccessYes, my windows user does have password. It all were working perfectly untill I restarted my remote PC - first time after Cloudberry installation. I could not even connect to it after the restart - RA service were working in background but it were no icon on taskabr right bottom corner. So I had to start RA from desktop shortcut and could connect again but only by PIN.
-
Newbie Guide to Unattended Remote AccessHello Sergey,
Here you can see Cloudberry settings on remote computer:
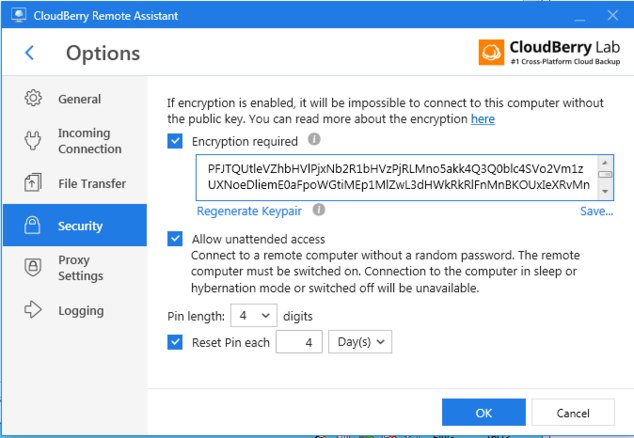
Here are the settings on my home computer:
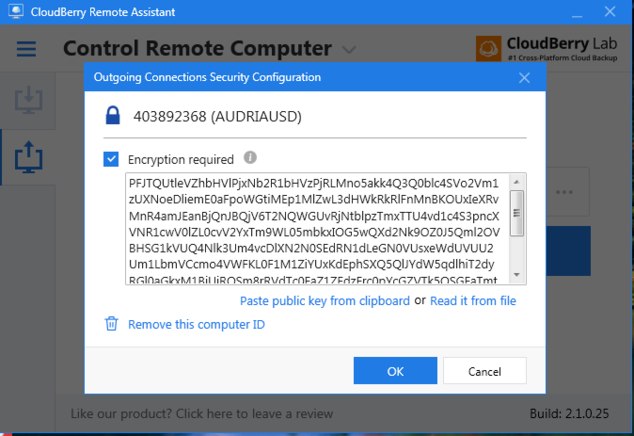
And here you can see a screenshot when I try to connect to remote computer:
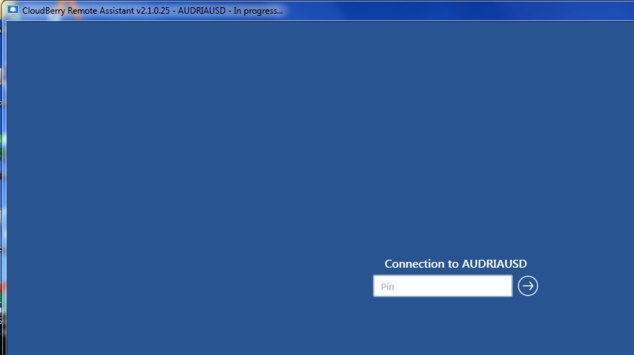
-
Newbie Guide to Unattended Remote AccessHello Sergey,
I have all settings like on this guide - ecryption On, unattended access On. But when I connect it still asks to enter Pin. -
Newbie Guide to Unattended Remote AccessMy unattended access is not working after I restarted remote computer. After the restart it always asks for PIN. I have even tried to generate the new encryption text but it didn't help. Encryption is enabled on both computers - remote and local. How can I fix it?
Antanas

Start FollowingSend a Message
- Terms of Service
- Useful Hints and Tips
- Sign In
- © 2025 MSP360 Forum


